|
|
I have just read the Presentation Zen blog post about PowerPoint.
One of the interesting suggestions was that it’s not effective to present the same information twice, so you don’t have notes covering what you say. Having a diagram that gives the same information is effective though because it gives a different way of analyzing the data. I looked at a couple of sets of slides that I have written and noticed that the ratio of text slides to diagram slides was 6:1 and 3:1 in favor of text, and that wasn’t counting the first and last slides that have the title of the talk and a set of URLs respectively.
So it seems that I need more and better diagrams. I’ll include most of the diagrams I use in my current SE Linux talks in this post with some ideas on how to improve them. I would appreciate any suggestions that may be offered (either through blog comments or email).
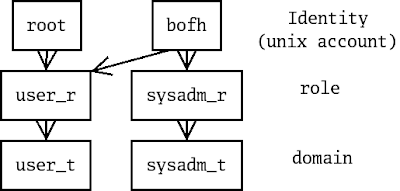 The above diagram shows how the SE Linux identity limits the roles that may be selected, and how the role limits the domains that may be entered. Therefore the identity controls what the user may do and in this example the identity “root” means that the user has little access to the machine (a Play Machine configuration). I think that the above is reasonably effective and have been using it for a few years. I have considered a more complex diagram with the “staff_r” role included as well and possibly including the way that “newrole” can be used to change between roles. So I could have the above as slide #1 about identities and roles with a more detailed diagram following to replace a page of text about role transition. The above diagram shows how the SE Linux identity limits the roles that may be selected, and how the role limits the domains that may be entered. Therefore the identity controls what the user may do and in this example the identity “root” means that the user has little access to the machine (a Play Machine configuration). I think that the above is reasonably effective and have been using it for a few years. I have considered a more complex diagram with the “staff_r” role included as well and possibly including the way that “newrole” can be used to change between roles. So I could have the above as slide #1 about identities and roles with a more detailed diagram following to replace a page of text about role transition.
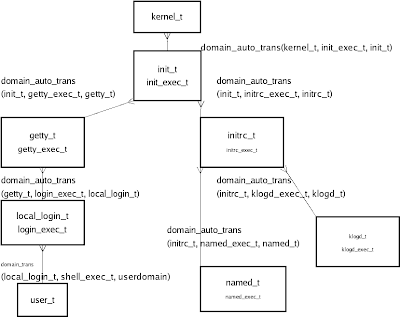 The above diagram shows the domain transitions used in a typical system boot and login process. It includes the names of the types and a summary of the relevant policy rules used to implement the transitions. I also have another diagram that I have used which is the same but without the file types and policy. In the past I have never used both in the one talk – just used one of the two and had text to describe the information content of the other. To make greater use of diagrams I could start with the simple diagram and then have the following slide have all the detail. The above diagram shows the domain transitions used in a typical system boot and login process. It includes the names of the types and a summary of the relevant policy rules used to implement the transitions. I also have another diagram that I have used which is the same but without the file types and policy. In the past I have never used both in the one talk – just used one of the two and had text to describe the information content of the other. To make greater use of diagrams I could start with the simple diagram and then have the following slide have all the detail.
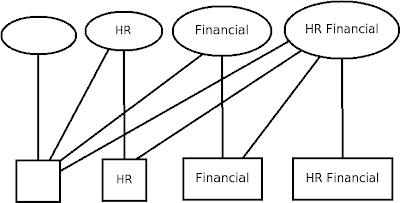 The above diagram simply displays the MCS security model with ellipses representing processes and rectangles representing files. The above diagram simply displays the MCS security model with ellipses representing processes and rectangles representing files.
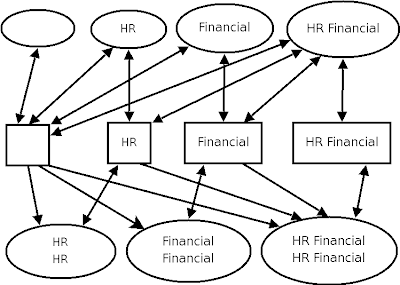 The above diagram shows a simplified version of the MMCS policy. With MMCS each process has a range with the low level representing the minimum category set of files to which it is permitted to write and the high level representing the files that it may read and write. So to write to a file with the “HR” category the process must have a low level that’s no higher than “HR” and a high level that is equal or greater than “HR“. The full set of combinations of two categories with low and high levels means 10 different levels of access for processes which makes for a complex diagram. I need something other than plain text for this but the above diagram is overly complex and a full set is even more so. Maybe a table with process contexts on one axis, file contexts on another and access granted being one of “R“, “RW” or nothing? The above diagram shows a simplified version of the MMCS policy. With MMCS each process has a range with the low level representing the minimum category set of files to which it is permitted to write and the high level representing the files that it may read and write. So to write to a file with the “HR” category the process must have a low level that’s no higher than “HR” and a high level that is equal or greater than “HR“. The full set of combinations of two categories with low and high levels means 10 different levels of access for processes which makes for a complex diagram. I need something other than plain text for this but the above diagram is overly complex and a full set is even more so. Maybe a table with process contexts on one axis, file contexts on another and access granted being one of “R“, “RW” or nothing?
I also have a MLS diagram in the same manner, but I now think it’s too awful to put on my blog. Any suggestions on how to effectively design a diagram for MLS? For those of you who don’t know how MLS works the basic concept is that every process has an “Effective Clearance” (AKA low level) which determines what it can write, it can’t write to anything below that because it might have read data from a file at it’s own level and it can’t read from a level higher than it’s own level. MLS also uses a high level for ranged processes and filesystem objects (but that’s when it gets really complex).
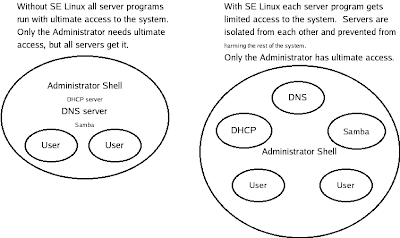 This last one is what I consider my most effective diagram. It shows the benefits of SE Linux in confining daemons in a clear and effective manner. Any suggestions for improvement (apart from fixing the varying text size which is due to a bug in Dia) would be appreciated. This last one is what I consider my most effective diagram. It shows the benefits of SE Linux in confining daemons in a clear and effective manner. Any suggestions for improvement (apart from fixing the varying text size which is due to a bug in Dia) would be appreciated.
The above diagrams are all on my SE Linux talks page, along with the Dia files that were used to create them. They may be used freely for non-commercial purposes.
If anyone has some SE Linux diagrams that they would like to share then please let me know, either through a blog comment, email, or a blog post syndicated on Planet SE Linux.
The online magazine EWeek has done a review of RHEL5. It’s quite a positive review which can be summarised as “good support for Xen as service (not an appliance), better value than previous versions with the licenses for multiple guests included, and SE Linux briefly got in the way but the Troubleshooting tool fixed it quickly and easily”.
The problem they had is that the SE Linux policy expects Xen images to be in /var/lib/xen/images, but the Xen configuration tools apparently didn’t adequately encourage them to use that directory. They stored the images somewhere else and SE Linux stopped it from working. The Troubleshooting tool did something that they didn’t describe and then it all worked.
Generally a very positive review of RHEL5 and a moderately positive review of SE Linux in RHEL5.
PS You might have to turn off JavaScript to view the link, the page has broken JavaScript code that takes an unreasonable amount of CPU time.
BOF stands for Birds Of a Feather, it’s an informal session run at a conference usually without any formal approval by the people who run the conference.
Often conferences have a white-board, wiki, or other place where conference delegates can leave notes for any reason. It is used for many purposes including arranging BOFs. To arrange a BOF you will usually write the title for the BOF and the name of the convenor (usually yourself if it’s your idea) and leave a space for interested people to sign their names. Even though there is usually no formal involvement of the conference organizers they will generally reserve some time for BOFs. Depending on the expected interest they will usually offer one or two slots of either 45 minutes or one hour. They will also often assist in allocating BOFs to rooms. But none of this is needed. All that you need to do is find a notice-board, state your intention to have a BOF at a time when not much else is happening and play it by ear!
My observation is that about half the ideas for BOFs actually happen, the rest don’t get enough interest. This is OK, one of the reasons for a BOF is to have a discussion about an area of technology that has an unknown level of interest. If no-one is interested then you offer the same thing the next year. If only a few people are interested then you discuss it over dinner. But sometimes you get 30+ people, you never know what to expect as many people don’t sign up – or have their first choice canceled and attend the next on the list!
To run a BOF you firstly need some level of expert knowledge in the field. I believe that the best plan is for a BOF to be a panel discussion where you have a significant portion of the people in the audience (between 5 and 15 people) speaking their opinions on the topic and the convener moderating the discussion. If things work in an ideal manner then the convener will merely be one member of the panel. However it’s generally expected that the person running the BOF can give an improvised lecture on the topic in case things don’t happen in an ideal manner. It’s also expected that the convener will have an agenda for a discussion drawn up so that if the panel method occurs they can ask a series of questions for members of the BOF to answer. My experience is that 8 simple questions will cover most of an hour.
One requirement for convening a BOF is that you be confident in speaking to an audience of unknown size, knowledge, and temperament. Although I haven’t seen it done it would be possible to have two people acting as joint conveners of a BOF. One person with the confidence to handle the audience and manage the agenda and another with the technical skills needed to speak authoritatively on the topic.
Some of the BOFs I have attended have had casual discussions, some have had heated arguments, and some ended up as lectures with the convener just talking about the topic. Each of these outcomes can work in terms of entertaining and educating the delegates.
But don’t feel afraid, one of the advantages of a BOF is that it’s a very casual affair, not only because of the nature of the event but also because it usually happens at the end of a long conference day. People will want to relax not have a high-intensity lecture. One problem that you can have when giving a formal lecture to an audience is nervous problems such as hyper-ventilating. This has happened to me before and it was really difficult to recover while continuing the lecture. If that happens during a BOF then you can just throw a question to the audience such as “could everyone in the room please give their opinion on X“, that will give you time for your nerves to recover while also allowing the audience to get to know each other a bit – it’s probably best to have at least one such question on your agenda in case it’s needed.
Note that the above is my personal opinion based on my own experience. I’m sure that lots of other people will disagree with me and write blog posts saying so. ;)
The facts which I expect no-one to dispute are:
- BOFs are informal
- Anyone can run one
- You need an agenda
- You need some level of expert knowledge of the topic
In a blog on infoworld the following strange statement appeared:
The US Constitution is clear that the reason for copyright/patent/etc. is to benefit creators of property, not users of property. I appreciate the reason: give creators a reasonable return on their investment.
Actually the US constitution seems to clearly say the opposite. Here is a link to section 8 of the US constitution. The important phrase is “To promote the progress of science and useful arts, by securing for limited times to authors and inventors the exclusive right to their respective writings and discoveries“.
There is no mention of providing benefits to creators of written works and inventions. The aim is clearly stated to promote the progress of science and useful arts and the exclusive right which operates for limited times is merely a method of achieving that aim.
James Dumay writes about Theo’s latest flame-war.
One interesting part of the debate was Theo’s response to this comment:
> We can dual license our code though and that is an
> acceptable license for Linux, the kernel.
Theo:
We? Sure, you can. But Reyk will not dual license his code, and most of the other people in the BSD community won’t either, because then they receive the occasional patch from a GPL-believer which is ONLY under the GPL license, and then they are no less screwed than they would be from the code granted totally freely to companies.
The difference of course is that when you give code to companies under the BSD license you will never know what is done to it, but GPL-only patches can still be used as inspiration for new code development. Sure GPL-only code can’t be copied into BSD-only code, but once you know where the bugs are they are easy to fix.
Towards the end of the debate Theo asks the following question:
David, if you found a piece of your code in some other tree, under a different license, would your first point of engatement be a public or private mail?
I can’t speak for David, but after reading the discussion I would probably start by blogging about such an issue.
Ingo Juergensmann has blogged in detail about the new release and the new DPL.
Sam Hocevar ran for DPL on a platform based on some significant new changes. It will be interesting to see what happens over the next year.
The release of Etch is an exciting milestone in Debian development. Among other things it has SE Linux working!
I’m going to try and arrange a party in Melbourne, Australia to celebrate. We also have a mailing list for Debian people in Melbourne, to subscribe send a message to debian-melb-request@taz.net.au with the subject subscribe. I’ll use that list for arranging the party, send me private email if you are not subscribed but want to attend.
If I enter “a < b” in blogger then it works, but if I want the < symbol to be next to some other text (EG for a #include line in C source) then it treats it as a HTML tag. The HTML code for a < symbol also doesn’t work. This doesn’t work regardless of whether I try entering HTML in the HTML editor or entering text in the “Compose” editor. I could deal with this problem if it forced me to strictly use one of the two editors available, but it fails in both!
Do other blog server programs have problems like this? I think that I need to change my blog server just to allow posting C source!
Also do any of the common blog servers allow a file upload? For most of my posts I do all the editing offline, so I’d rather just upload a HTML file instead of pasting the text into the blog editor (and then manually fixing the situations where it’s idea of formatting differs from mine). If such an upload mode also supported getting a file via HTTP then that would be convenient too. The option of editing a file on a remote server with vi, exporting it via Apache, and then getting it to the blog server via HTTP would work well for me in some important situations.
Update: It sucks more than I thought. The feed misses the “less than” character between “a” and “b” in the above paragraph. My list of requirements in this regard now includes the ability to use such characters in a feed. Actually I want to go the whole hog and be able to include samples of HTML in my blog entries and have them display correctly in the feed.
In Debian bug 418210 there is discussion of what constitutes a cluster.
I believe that the node configuration lines in the config file /etc/ha.d/ha.cf should authoritatively define what is in the cluster and any broadcast packets from other nodes should be ignored.
Currently if you have two clusters sharing the same VLAN and they both use the same auth code then they will get confused about which node belongs to each cluster.
I set up a couple of clusters for testing (one Debian/Etch and the other Debian/unstable) under Xen using the same bridge device – naturally I could set up separate bridges – but why should I have to?
I gave each of them the same auth code (one was created by copying the block devices from the other – they have the same root password so there shouldn’t be a need for changing any other passwords). Then things all fell apart. They would correctly determine that they should each have two nodes in the cluster (mapping to the two node lines), but cluster 1 would get nodes ha1 and ha2-unstable even though it had node lines for ha1 and ha2.
I have been told that this is the way it’s supposed to be and I should just use different ports or different physical media.
I wonder how many companies have multiple Heartbeat installations on different VLANs such that a single mis-connected cable will make all hell break loose on their network…
At http://tanso.net/selinux/ Jan-Frode Myklebust has documented his work in creating new SE Linux policy to run Googleearth on Red Hat Enterprise Linux 5. He discussed this with us on #selinux in irc.freenode.net (the main SE Linux IRC channel).
One of his later IRC comments was:
<janfrode> btw erich, the reason for creating this googleearth module was mostly triggered by your apparmor blog entry.. I wanted to see how much more difficult it would be to create policies in selinux compared to apparmor, and must say it wasn’t too hard.
“erich” refers to Erich Schubert. His AppArmor blog entry is currently the top entry in his SE Linux list.
This morning after having had my car parked in the sun for a couple of hours I poured water on the rear window to cool it (as described in this post). When I did so the mist that rose up from the window spiraled up in a way that was similar to a cyclone (but on a much smaller scale).
Would this have been caused by the steam rising off my car after I poured the water on? Or might the air have been moving in that pattern before and merely have been revealed by the water vapor?
It’s a pity I didn’t have my camera. My phone-camera doesn’t have anything close to the quality needed to make a movie of this (it would be doubtful even with my regular camera).
|
|
 The above diagram shows how the SE Linux identity limits the roles that may be selected, and how the role limits the domains that may be entered. Therefore the identity controls what the user may do and in this example the identity “root” means that the user has little access to the machine (a Play Machine configuration). I think that the above is reasonably effective and have been using it for a few years. I have considered a more complex diagram with the “staff_r” role included as well and possibly including the way that “newrole” can be used to change between roles. So I could have the above as slide #1 about identities and roles with a more detailed diagram following to replace a page of text about role transition.
The above diagram shows how the SE Linux identity limits the roles that may be selected, and how the role limits the domains that may be entered. Therefore the identity controls what the user may do and in this example the identity “root” means that the user has little access to the machine (a Play Machine configuration). I think that the above is reasonably effective and have been using it for a few years. I have considered a more complex diagram with the “staff_r” role included as well and possibly including the way that “newrole” can be used to change between roles. So I could have the above as slide #1 about identities and roles with a more detailed diagram following to replace a page of text about role transition. The above diagram shows the domain transitions used in a typical system boot and login process. It includes the names of the types and a summary of the relevant policy rules used to implement the transitions. I also have another diagram that I have used which is the same but without the file types and policy. In the past I have never used both in the one talk – just used one of the two and had text to describe the information content of the other. To make greater use of diagrams I could start with the simple diagram and then have the following slide have all the detail.
The above diagram shows the domain transitions used in a typical system boot and login process. It includes the names of the types and a summary of the relevant policy rules used to implement the transitions. I also have another diagram that I have used which is the same but without the file types and policy. In the past I have never used both in the one talk – just used one of the two and had text to describe the information content of the other. To make greater use of diagrams I could start with the simple diagram and then have the following slide have all the detail. The above diagram simply displays the MCS security model with ellipses representing processes and rectangles representing files.
The above diagram simply displays the MCS security model with ellipses representing processes and rectangles representing files. The above diagram shows a simplified version of the MMCS policy. With MMCS each process has a range with the low level representing the minimum category set of files to which it is permitted to write and the high level representing the files that it may read and write. So to write to a file with the “HR” category the process must have a low level that’s no higher than “HR” and a high level that is equal or greater than “HR“. The full set of combinations of two categories with low and high levels means 10 different levels of access for processes which makes for a complex diagram. I need something other than plain text for this but the above diagram is overly complex and a full set is even more so. Maybe a table with process contexts on one axis, file contexts on another and access granted being one of “R“, “RW” or nothing?
The above diagram shows a simplified version of the MMCS policy. With MMCS each process has a range with the low level representing the minimum category set of files to which it is permitted to write and the high level representing the files that it may read and write. So to write to a file with the “HR” category the process must have a low level that’s no higher than “HR” and a high level that is equal or greater than “HR“. The full set of combinations of two categories with low and high levels means 10 different levels of access for processes which makes for a complex diagram. I need something other than plain text for this but the above diagram is overly complex and a full set is even more so. Maybe a table with process contexts on one axis, file contexts on another and access granted being one of “R“, “RW” or nothing? This last one is what I consider my most effective diagram. It shows the benefits of SE Linux in confining daemons in a clear and effective manner. Any suggestions for improvement (apart from fixing the varying text size which is due to a bug in Dia) would be appreciated.
This last one is what I consider my most effective diagram. It shows the benefits of SE Linux in confining daemons in a clear and effective manner. Any suggestions for improvement (apart from fixing the varying text size which is due to a bug in Dia) would be appreciated.